Page Content
CONTENTS
Issuing
ETMS, ATM, POS, mPOS, SOFTPOS
ETMS
Enterprise Terminal Management System (ETMS) is a technology that helps Point of Sale (POS) service providers to acquire and manage different crucial elements, such as:- Payments
- Transaction permissions
- Europay, MasterCard® and Visa® (EMV) parameters
- Transaction tables
- Merchant information
ETMS Functionalities
ETMS products offer a broad range of functionalities designed to automate vital processes. Quality solutions are known to offer:- Remote terminal management
- Multi-vendor support
- Multi-currency support
- Multiple communication channels
- Data analysis reporting
- Role-based access
How Do ETMS Solutions Work?
When people make purchases using their debit or credit cards at a terminal, the ETMS processes the transaction. It works with the payment gateway to authorise the operation and then route it to its respective processor. The ETMS is responsible for storing data regarding all the terminals that are connected to it. It includes:- Software version
- IP address
- Location
Automate Terminal Updates
When deploying ETMS products, businesses must address the ability to manage data upgrades related to firmware on payment devices and EMV standards. It is crucial because if the technology isn’t up-to-date, it may leave customers vulnerable to processing issues and security breaches. Failing to make regular updates may lead to compliance problems and card brand fines, which are passed down to merchants by processors and acquiring banks. ETMS products are embedded platforms that run a complex software stack. As with any software stack, it requires updates to remain compliant with the latest EMV parameters. General bug fixes and security vulnerability patches must also be applied to payment terminals. All EMV-enabled solutions require frequent updates to cover various new data elements known to change periodically, like Data Object Lists and CA Public Keys. Having the right data elements is critical to correct cryptographic operation.Who Uses ETMS Solutions?
Different businesses can benefit from deploying ETMS products.- Retails that remotely manage a large number of terminals
- Hospitality organisations that need to accept payments in multiple locations
- Transport companies that need to accept payments at different points in their routes
- Businesses with mobile sales representatives that need to accept payments on the go
Automate Teller Machine
An automated teller machine (ATM) is an electronic telecommunications device developed to help the customers of financial institutions perform different operations without direct interaction with bank staff. People can use an ATM for:- Deposits
- Funds transfers
- Account information inquiries
- Balance inquiries
- Cash withdrawals
History
The concept of out-of-hours cash distribution was developed from bankers’ needs in the United Kingdom, Sweden, and Japan. In 1960, Armenian-American inventor Luther George Simjian created an automated deposit machine that could accept coins, cash, and cheques. The device didn’t have any cash dispensing features. He filed for a U.S. patent on 30 June 1960 and was granted it on 26 February 1963. The launching of the machine, called Bankograph, got delayed by a couple of years since Universal Match Corporation was acquiring Simjian’s company Reflectone Electronics Inc. An experimental device was installed in New York City in 1961 by the City Bank of New York but was removed after six months as not enough customers used it. In 1962 Adrian Ashfield came up with a card system to securely identify a user and control and monitor the dispensing of services or goods. The invention was granted a UK patent 959,713 in June 1964 and assigned to Kins Developments Limited. Barclays Bank installed a cash machine in Enfield Town on 27 June 1967. It became recognised as the world’s first ATM. Its invention is credited to John Shepherd-Barron. Transactions were set in motion by inserting paper cheques a cashier or teller issued. The cheques were marked with carbon-14 for security and machine readability, a technique which was later replaced by the PIN code. Engineers working at Smiths Group developed the idea of a PIN stored on cards in 1965. At the time, the company was working on their own cash machine, Chubb MD2. James Goodfellow is credited as the man behind the invention of the PIN code. The main principle behind the system was to enable the verification of users’ debit accounts without human intervention.Propagation
Cash machines manufactured by British and Swedish companies rapidly spread worldwide. Scotland, Australia, and Spain were among the first countries to test them. Banks used different methods to stimulate customers to use the machines. The Bank of Scotland, for example, supplied users with £10 vouchers.Docutel in the United States
After witnessing firsthand the success of cash-dispensing machines in Europe, Docutel, a subsidiary of Recognition Equipment Inc., called upon Donald Wetzel to pioneer an American ATM. On 2 September 1968, Chemical Bank installed Docutel’s prototype cash machine at its Rockville Centre, New York branch. The first ATMs were designed to dispense a fixed amount of cash only after customers had inserted a specially coded card. In the beginning, Chemical executives were reluctant to transition to electronic banking due to the high cost of the machines. They were also concerned that their clients would be resistant to using ATMs. To demonstrate their confidence in the devices, Chemical used the first four production ATMs in a marketing test to prove their reliability. The trial was successful, as customers were even prepared to pay a usage fee. Based on the generated results, banks throughout the United States began experimenting with and installing cash-dispensing machines. By 1974, Docutel had acquired 70% of the U.S. market. However, because of the 1970s worldwide recession and its dependence on a single product, the company was forced to merge with the U.S. subsidiary of Olivetti.Further Advances
In April 1971, the now-defunct Japanese company Busicom began manufacturing ATMs based on the first commercial microprocessor, the Intel 4004. Busicom produced these microprocessor-based machines for several customers, the most notable being NCR Corporation. Around that time, Mohamed Atalia created the “Atalla Box”, a hardware security module that encrypted PIN and ATM messages. It also protected offline devices with an un-guessable PIN-generating key. In March 1972, Atalla filed U.S. Patent 3,938,091 for his invention, which featured an encoded card reader and described a system that uses encryption methods to assure telephone link security while inputting personal ID information that is transmitted to a remote location for verification. He established Atalla Corporation (now Utimaco Atalla) in 1972, and commercially launched the “Atalla Box” in 1973. The product, a customer identification system and card reader that provided terminals with PIN and plastic card capabilities was branded Identikey. It consisted of two PIN pads, an intelligent controller, a card reader console, and a built-in electronic interface package. Its implementation on ATMs replaced manual entry of account numbers and minimised possible keystroke errors. The “Atalla Box” success led to the broad adoption of hardware security modules in manufacturing cash-dispensing machines. As of 2014, Atalla’s products protect 250 million card transactions daily and secure most ATM operations. On 3 February 1979, the first switching system to allow shared cash machines between banks began production in Denver, Colorado. The Colorado National Bank and Kranzley and Company undertook the initiative. The Royal Bank of Scotland installed a new ATM in 2012 that enabled users to withdraw cash up to £130 without a card by typing a six-digit code requested via their smartphones.Location
ATMs can be installed at any location but are most commonly placed inside or near banks, shopping centres, transportation hubs, metro stations, restaurants, petrol stations, grocery stores, etc. Cash-dispensing machines are also found in U.S. Navy ships and cruise shops. On-premises ATMs are usually more advanced, offering multiple options that complement the services banks and their branches provide. They are also more expensive. Financial institutions install cheaper off-premises single-function machines at locations where cash is needed. In the United States, Canada, and some Gulf countries, banks may have drive-thru lanes that offer access to ATMs using an automobile. Recently, more and more countries have been installing solar-powered cash machines in rural areas. This trend is especially noticeable in India and Africa. The world’s highest ATM is situated at the Khunjerab Pass in Pakistan. Placed at an elevation of 4,693 metres (15,397ft) by the National Bank of Pakistan, the machine is built to function in temperatures as low as -40 degrees Celsius. Independent ATM deployers, not affiliated with banks and other financial institutions, are known to deploy and maintain white-label machines for different businesses.Financial Networks
Most ATMs are linked to interbank networks. This connection allows users to deposit and withdraw money from machines that don’t belong to the banks where they have their accounts or in the countries where their funds are held. Cash-dispensing machines rely on the authorisation of a transaction by the card issuer or other authorising entity on a communications network. It is often executed via the ISO 8583 messaging system. Many financial institutions charge ATM usage fees. In some cases, the fees apply only to users who aren’t clients of the bank operating the machine. In other cases, the fees pertain to anyone using the ATM. To enable a broader range of devices to link to their systems, some interbank networks have passed protocols expanding the definition of cash-dispensing machines. According to the new rules, an ATM is a terminal that either uses the vault or cash drawer within an establishment or has the vault within its footprint. Usually, ATMs connect directly to their host or ATM Controller on ADSL, leased line, or dial-up modem over a telephone line. Leased lines are preferable to Plain Old Telephone Service (POTS) lines because they need less time to establish a link. Less-trafficked machines typically rely on a dial-up modem connection since leased lines are more expensive. However, this problem is expected to be solved by deploying high-speed Internet VPN connections as they are expected to become more ubiquitous. Standard lower-level layer communication protocols used by ATMs to communicate to banks are:- Systems Network Architecture (SNA) over Synchronous Data Link Control (SDLC)
- TC500 over Async
- TCP/IP over Ethernet
- New York Currency Exchange (NYCE)
- Pulse
- Visa Plus
- Mastercard Cirrus
- Interac
- Armed Forces Financial Network (AFFN)
- Interswitch
- LINK
- STAR
- BancNet
- MegaLink
Global Use
No government or internationally-complied statistics show the number of ATMs in use worldwide. Estimates developed by the ATM Industry Association (ATMIA) place the number of machines in use at 3 million. Financial institutions divide the world into seven regions based on deployed features, usage statistics, and penetration rates to simplify the analysis of worldwide ATM usage. Canada, Europe, Japan, and the United States are the four regions with the highest numbers of machines per million people. Despite large numbers of ATM units, the Asia/Pacific and Latin America areas demand additional machines. Conversely, Macau has the highest density of ATMs at 254 machines per 100,000 adults. With the invention and introduction of cashless payment solutions, the usage and number of cash-dispensing machines started to decline. It first happened in developed countries, contrasting with many African and Asian countries where ATM numbers were still increasing. As of 2021, the number of machines used worldwide is still dropping.Hardware
ATMs are usually made up of the following components:- Central Processing Unit (CPU) that controls transaction devices and the user interface
- Chip or magnetic card reader to identify customers
- PIN pad for accepting and encrypting personal identification number EPP4. This device is manufactured as part of a secure enclosure.
- Sensors and indicators
- Housing
- Vault to store machinery and components with restricted access
- Secure cryptoprocessor
- Display to facilitate the execution of transactions
- Record printer to offer users transaction receipts
- Function key buttons or touchscreen
- Magnetic, seismic, thermal, or gas security sensors
- Dispensing mechanism to provide cash or other valuables
- Locks to control access to the vault
- Electronic or solid-state journaling systems to accrue all records of activity
- Deposit mechanism (cheque processor and bulk note acceptor) to allow users to make deposits
Software
In the past, ATMs were manufactured to feature Real-time Multitasking eXecutive (RMX) or Operating System/2 (OS/2) platforms. Today, the majority of cash-dispensing machines worldwide use Microsoft Windows. Studies show that in early 2014, 95% of ATMs were running Windows XP. The remaining 5% operate with older versions of the Windows OS, like Windows NT, Windows CE, or Windows. It is despite Microsoft currently supporting only Windows 10 and Windows 11. The computer industry security view is that general public desktop operating systems are at greater risk when used on cash-dispensing machines than other systems, such as real-time operating systems (RTOS). ATM manufacturers and owners are also using Linux. For example, Banrisul, the largest bank in southern Brazil, recently replaced its MS-Dos operating machines with their Linux-running counterparts. Banco do Brasil is also migrating their ATMs to Linux. In addition, Vortex Engineering, an India-based company, produces machines that operate exclusively on Linux. Common application layer transaction protocols like Diebold 911, Diebold 912, NCR, NDC, or NDC+ provide emulation of older generations of hardware on newer platforms. They use incremental extensions developed over time to address new capabilities, even though organisations like NCR continuously enhance their protocols by issuing new versions. Most prominent ATM manufacturers offer software packages that deploy these rules. More recent regulations, such as IFX, have yet to find reception by transaction processors. Since manufacturers shifted to a more standardised software base, financial institutions have been highly interested in the ability to select the application programs that run their machines. CEN XFS offers a common API for accessing and controlling the different components of an ATM. J/XFS is a Java implementation of the CEN XFS API. Cash-dispensing machine hardware vendors have different iterations of the XFS standard. These interpretations mean that ATM applications usually use middleware to even out dissimilarities among various platforms. Software applications can evolve and become more intelligent with the onset of XFS and Windows operating systems on cash-dispensing machines. This tendency has created a new breed of ATM programmable applications. They allow for an entirely new host of applications that enable machines to do more than only communicate with the ATM switch. For example, devices can connect to video banking systems and content servers. Notable ATM software that runs on XFS platforms are:- Triton PRISM
- NCR APTRA Edge
- Diebold Agilis EmPower
- KAL Kalignite Software Platform
- Wincor Nixdorf ProTopas
- Absolute Systems AbosoluteINTERACT
- Euronet FTS
- Phoenix Interactive VISTAatm
- Intertech inter-ATM
- With the switch of ATMs to industry-standard computing ecosystems, many institutions have raised concerns about the integrity of the machine’s software stack.
Impact on Labour
Counter-intuitively, the number of human bank tellers in the United States has grown from approximately 300,000 in the 1970s to an estimated 600,000 in 2010. The contributing factor to his phenomenon is the invention of the ATM. Since cash-dispensing machines allow branches to operate with fewer tellers, banks can open more branches, which results in hiring more personnel to handle non-automated tasks.Security
Securing related to ATMs has several dimensions. Cash-dispensing machines practically demonstrate different security features and concepts working in unison.Physical
Early ATM security focused on ensuring the terminals resisted physical attacks since they are prone to ram-raiding. Another attack method used on cash-dispensing machines is plofkraak. It’s when all openings are sealed with silicone, and the vault is filled with combustible gas or explosives are attached to, inside, or near the ATM. The gas and explosives are then ignited, and the vault is distorted or opened by the force of the explosion. Plofkraak is used in countries like the Netherlands, Belgium, France, Denmark, Australia, Germany, and the United Kingdom. Plofkraak and other gas attacks can be averted through different gas explosion prevention devices. These systems use sensors to detect explosive gas and neutralise them by releasing a special suppression chemical that alters the composition of the gas and makes it ineffective. Modern ATM physical security denies thieves the ability to use stolen money. Using various Intelligent Banknote Neutralisation Systems, financial institutions and cash-dispensing machine owners can render stolen money useless. The most common technique is storing the cash in cassettes, which dye the banknotes when opened incorrectly. Another common practice is keeping the ATM filling schedules a secret and varying their parameters.Transactional Secrecy and Integrity
The integrity of secure cryptoprocessors is the main factor behind the security of ATM transactions. Cash-dispensing machines use general commodity components that sometimes aren’t classified as “trusted systems.” To prevent fraud, many jurisdictions worldwide require the encryption of personal information. Sensitive information in ATM transactions is typically encrypted with Data Encryption Standard (DES), but recent transaction processors usually require Triple DES. Remote Key Loading techniques can be deployed to ensure the secrecy of the initialisation of the encryption keys in the cash-dispensing machines. Message Authentication Code (MAC) or Partial MAC may also be implemented to ensure messages that have not been modified while in transit between the ATM and the financial network.Customer Identity Integrity
Man-in-the-middle attacks regarding cash-dispensing machines are made when criminals attach fake keypads or card readers to functioning devices. Manufacturers combat such actions by installing countermeasures to protect their equipment. Finger, iris, palm vein pattern, and facial recognition technologies are used in some countries as alternative methods to confirm the identity of cardholders. While efficient, these types of security devices are known to be expensive. Cheaper, mass-produced equipment developed to expose the presence of foreign objects in the front of ATMs is widely used, as tests have shown a 99% detection rate for all kinds of skimming devices.Device Operation Integrity
Openings on the user’s side of cash-dispensing machines are often fitted with mechanical shutters to avert tampering with the mechanisms. Alarm sensors are installed inside ATMs to alert operators when they are opened by unauthorised personnel. To deter hackers, cash-dispensing machines have a built-in firewall that locks the ATM when it detects malicious attempts to break into the device remotely. Governments and ATM operating bodies set the rules determining what is to be done when integrity systems fail. Depending on the laws, a bank may or may not be held liable when:- An attempt is made to dispense a client’s money from the machine
- An attempt is made to dispense a client’s money while it gets outside the ATM’s vault
- An attempt is made to dispense a client’s money when it was exposed in a non-secure fashion
- They are incapable of determining the condition of the money after a failed transaction
Customer Security
Security cameras and guards are the most common feature to ensure the safety of ATM users. Some banks install cash-dispensing machines in their lobbies, which may be accessible 24 hours a day. These areas have substantial security camera coverage and, during work hours, have a security guard. Lobbies that aren’t guarded are equipped with doors that can only be opened from the outside by inserting the bank card into a wall-mounted scanner.Jackpotting
Jackpotting is a term used to describe a specific method criminals use to steal money from cash-dispensing machines. The wrongdoers gain physical access via a small hole drilled in the ATM. Then, they disconnect the device’s hard drive and replace it with an external drive using an industrial endoscope. Then depress an internal button that restarts the machine under their control. Once rebooted, they can have the ATM dispense all of its money. In recent years, to prevent jackpotting, manufacturers encrypt the hard disk. It makes creating the software necessary for jackpotting more complex, thus, boosting the device’s security capabilities.Uses
ATMs were initially created as cash dispensers. Since then, they have evolved to provide many other bank-related services, such as:- Printing or ordering bank statements
- Updating passbooks
- Paying routine bills, taxes, and fees
- Cheque processing
- Cash advances
- Paying fully or partially credit balances
- Depositing currency acceptance, recognition, and recycling
- Transferring money between accounts
- Donate to charities
- Load a monetary value into stored-value cards
- Add pre-paid mobile phone credit
- Purchase items like:
- Lottery, movie, concert, and train tickets
- Gold
- Postage stamps
- Shopping mall gift certificates
- Videoconferencing with human tellers
- Cheque/cash acceptance
- Bar code scanning
- Biometrics
- On-demand printing of tickets, traveller cheques, and other “items of value”
- Co-ordination of ATMs with mobile phones
- Dispensing of phone cards and other media
- CRM
- Games
- Promotional features
- Integration with non-banking equipment
- Pharmacy dispensing
Reliability
Before a cash-dispensing machine is installed, it undergoes extensive testing with test money to check whether the backend computer systems allow it to perform transactions. Bank clients are known to expect high levels of reliability from ATMs, which incentivises manufacturers to limit the potential for machine and network failures. Cash-dispensing machines and supporting electronic financial networks are usually very reliable. Industry benchmarks measure 98.25% customer availability for ATMs and up to 99.999% availability for host systems that manage the device. This said, there is always a margin for human or mechanical error. There have been cases of machines dispensing money without debiting the account or giving higher-value notes due to improper loading of money cassettes. Furthermore, there are records of hard disk, card transport mechanism, keypad, software, and envelope deposit mechanism failures, although rare. Some ATMs have a roll-paper journal that records each transaction to improve reliability. It allows financial institutions and their clients to settle disputes based on the data in the journal. Newer models record transactions on electronic journals to spare the cost of supplying the device with paper. Bill validation technology is used to ensure the authenticity of the cash before it is stocked in machines. ATMs with cash recycling capabilities include this technology. Still, devices can dispense counterfeit banknotes, especially if they are stocked and wholly managed by outside companies instead of banks. ——————————————————————Point of Sale (POS)
The Point of Sale (POS) is when and where the purchase is completed. At the POS, the merchant or service provider calculates the amount owed by the customer, indicates the amount, may draft an invoice, and describes the options for the client to pay. After receiving the payment, the merchant or service provider issues a receipt for the transaction, which can be printed or sent electronically, depending on the technology used. To calculate the sum owned by a customer, the merchant may use different devices like:- Weighing scales
- Barcode scanners
- Cash registers
- POS cash registers (POS systems).
- Cash payment terminals
- Card payment terminals
- Touch screen terminals
- Inventory management
- Customer relationship management (CRM)
- Warehousing
- Financial reporting
- Financing
Terminology
A POS system’s fundamental definition is hardware or software that enables the recording and processing of transactions between companies and their customers at the moment in which goods or services are purchased. Many POS vendors refer to their products as “retail management systems,” which is more accurate since the software does more than simply process sales. Newer software comes with a multitude of functionalities, like:- Membership management
- Supplier recording
- Bookkeeping
- Stock transfer order issuing
- Quotation issuing
- Purchase order issuing
- Hide barcode label creation
- Sale reporting
- Inventory management
- Outlet networking/linkage
History
POS Software Before the 1990s
Early electronic cash registers (ECR) were limited in communication and function capabilities and were controlled by proprietary software. In August 1973, IBM launched the IBM 3650 and 3660 store systems. They were the first commercial use of client-server technology, local area network (LAN) simultaneous backup, remote initialisation, and peer-to-peer communications. William Brobeck and Associates built one of McDonald’s first microprocessor-controlled cash register systems in 1974. It used the Intel 8008, the forerunner to the Intel 8088 processor later used in the original IBM Personal Computer. Each station in the restaurants had its own device, which displayed the entire order for a customer. Up to eight cash registers were connected to one of the two interconnected computers so that prices, taxes, and printed reports could be handled from any device by setting it on Manager Mode. In 1986, Gene Mosher developed the first graphical POS software. It featured a colour touchscreen widget-driven interface that enabled the configuration of widgets representing menu items without low-level programming. The software was first demonstrated in public at Fall Comdex, 1986, in Las Vegas, Nevada, at the Atari Computer booth. Soon after, it was installed in restaurants in Canada and the United States. During the same year, IBM introduced its 468x series of POS equipment. The technology was based on FlexOS 1.xx and Digital Research’s Concurrent DOS 286 and had a modular real-time, multi-tasking, multi-user operating system.POS Software Post 1990s
The 1990s saw a revolution in POS technology as a broad range of applications were developed on platforms like Unix and Windows. The availability of local processing power, networking, graphical user interface, and local data storage made it possible to create flexible, highly functional systems. The cost of the technology also declined as all components could now be bought off-the-shelf. IBM adopted FlexOS 2.32 as the basis of their IBM 4690 OS in their 469x series of POS terminals in 1993. They developed the technology until 2014, then sold it to Japanese conglomerate Toshiba, who supported it until 2017. With a more competitive market and increased options for commodity hardware, POS system manufacturers started paying more attention to the user interaction between employees and POS terminals. Touchscreens and larger displays became the norm during the 1990s. The introduction of Graphical User Interface (GUI) technology considerably reduced learning time, positively impacting the cost of deploying and utilising POS devices. The main parameters that modern POS systems must meet may include:- High operating speed
- Consistent operating speed
- Ease of use
- Remote supportability
- Reliability
- Multiple functionality
- Low cost
- Sale
- Inventory
- Stock counting
- Vendor ordering
- Customer loyalty
- Reporting
- Processing monetary transactions
- Scheduling of facilities
- Allocation of resources and facilities
- Recording services provided to customers
- Scheduling services to be provided to customers
- Tracking of goods
- Tracking of processes
- Tracking of debts and outstanding payments
- Invoicing
- Membership discounts
- Point accumulation and usage
- Quantity and promotional discounts
- Cash rounding up
- Mix and match offers
- Invoice and delivery order issuance without outstanding amount
Post-1980s Hardware Interface Standardisation
Retailers and vendors are trying to standardise the development of computerised POS systems. They also aim to simplify the interconnecting of POS devices. JavaPOS and OPOS are two such initiatives, both of which comply with the UnifiedPOS standard led by The National Retail Foundation. OPOS was the first commonly adopted standard. Microsoft, Epson, Fujitsu-ICL, and NCR Corporation created it. OPOS is a COM-based interface, making it compatible with all COM-enabled programming languages for Windows. It was launched in 1996. JavaPOS was developed by IBM, NCR Corporation, and Sun Microsystems in 1997 and released in 1999. It’s largely platform-independent as it’s for Java, what OPOS is for Microsoft Windows. There are various communication channels POS systems use to control peripherals:- UTC Standard
- UTC Enhanced
- Logic Controls \ BemaTech
- AEDEX
- ICD 2002
- Epson Esc/POS
- HP
- ADM 787/788
- CD 5220
- DSP-800
User Interface Design
The design of the sale window is undoubtedly the most important for the end user. The interface is vital compared to those used in other software packages, such as word editors or spreadsheet programs, when execution speed isn’t as essential for business performance. It’s common to see queues of customers at companies based at prime locations. The faster a sale is completed, the shorter the queue time, positively affecting overall client satisfaction. It also takes less space, providing shoppers and staff with a more comfortable and enjoyable environment. High-traffic businesses like cafes and grocery outlets need to process sales quickly, meaning the User Interface (UI) flow is often developed to feature few popups or interruptions to enable the operator to handle and execute transactions swiftly. Clean, fast-paced designs may sometimes come at the expense of other capabilities that end-users may want. Such functionality can be:- Discounts
- Membership and loyalty schemes
- Access to commission records
- Points accumulation
Post-2000s Cloud-Based POS Systems
The advancement of cloud computing has allowed the possibility of Electronic Point of Sale (EPOS) systems to be deployed as a software service. EPOS platforms are designed to be accessed directly from the Internet using any browser. Cloud-based POS systems are independent of framework and operating system limitations. Since they are based in the cloud, they are generally subscription-based, meaning they also offer ongoing technical support. Compared to conventional cash registers, which are considerably more affordable but can only process sales and print receipts, POS systems include automatic inventory and stock updating, remote computer access to real-time reports, customer loyalty features, and staff timesheets. EPOS systems are developed to be compatible with a wide selection of POS hardware, including tablets. They help POS platform owners expand to various mobile devices. They can also act as barcode readers via a built-in camera and as payment terminals through NFC technology or an external card reader. Several POS companies develop their software specifically to be cloud-based. Manufacturers that launched their products pre-2000s have since adapted their software to the technology. Cloud-based POS products differ from traditional POS devices because user data isn’t stored locally. Instead, it’s saved on a remote server. In addition, EPOS isn’t run locally, meaning no installation is required. Depending on the vendor and the contract terms, compared to conventional on-site POS installation, the software is likely to be continuously updated by the developer with newer and more practical features that will enhance computing performance and limit bugs and errors. Other advantages of cloud-based POS systems are the instant centralisation of data (a vital process to chain stores and franchises), the lower start-up costs, and the ability to access information from anywhere as long as an Internet connection is available. EPOS requires an Internet connection. For this reason, businesses must use devices with 3G connectivity in case the machine’s primary Internet goes down. Besides being significantly less expensive than traditional POS systems, the real perk of EPOS is that numerous developers create software applications for it. Many experts describe cloud-based POS systems as future-proof as new features and applications are being consistently conceived and built. During the last decade, several prominent emergency EPOS systems were launched. They’re mainly designed for restaurants and small and medium retail companies with relatively simple sales procedures. However, similar software for enterprise-level organisations is currently lacking in the market. “Enterprise-level” means systems capable of handling many inventory records, generating reports like sales analytics against inventory for single and multiple outlets interlinked for administration by the headquarters of the business. POS vendors offering cloud-based solutions should always have firm backup plans for the breakdown of their remote servers. Sometimes, major data centres can cease to function altogether. Companies may choose to have an on-site installation alongside their EPOS systems to ensure continuous operations. Another more innovative contingency approach is having the developer install a trimmed version of the POS system on the cashier’s computer at each outlet. This allows the remote servers to update daily local databases with information concerning inventory and customer memberships. Even though EPOS systems save end users startup costs and technical challenges compared to their on-premise counterparts, there is always the risk that if a cloud-based solution vendor closes, it may result in the immediate termination of services. This possibility is a handicap compared to on-site POS platforms, as businesses can use them without the manufacturer or vendor. Another aspect to consider is that EPOS systems expose databases to the vendor and hosting service company. That means it’s of paramount importance to secure critical business data such as, but not limited to:- Supplier names
- Top selling items
- Customer relationship procedures
- Prices
- Client names
mPOS Terminals
A Mobile Point-of-Sale (mPOS) can be anything from a smartphone to a tablet to a dedicated wireless device that serves as a cash register or electronic POS terminal wirelessly. mPOS technology is useful for businesses that must accept transactions on the go. To deploy mPOS, companies need a stable internet connection, a payment card reader, and an application downloaded and installed on the device they wish to use as a cash register or electronic payment terminal. The POS app and reader will work in tandem to enable the acquisition of payments. Businesses can also pair their devices with additional POS hardware, such as cash drawers and barcode scanners.How Does an mPOS Work
An application can convert any smartphone or tablet into a mobile point-of-sale. Usually, when a company registers with a POS app, the vendor provides a card reader that plugs directly into the device through the audio jack. Once the reader is installed, the smartphone or tablet instantly becomes capable of accepting credit and debit card payments. Some mPOS developers also give optional hand-held docking stations (known as sleds) that allow users to print receipts and read barcodes. Depending on the software, an mPOS can function as a standalone device that is simply connected to a bank account, or it can be integrated and become part of a more extensive POS system.Benefits of mPOS
mPOS technology enables sales and service organisations to execute financial operations more versatilely and without being constrained to a single location. It improves customer experience by limiting waiting time, offering different payment options, and accelerating execution time. Last but not least, it frees up valuable real estate that countertop POS terminals would otherwise occupy. Because of their portability, mPOS devices are perfect for companies that are constantly on the move, like food trucks, contractors, market vendors, wellness service providers, etc. The technology allows such professionals to accept transactions on the spot via different payment mediums. With the continuously growing popularity of mobile wallets and contactless payments, such as Apple Pay and Google Pay, it’s safe to say that mPOS technology is better fitted to accommodate clients who wish to conduct transactions by tapping on their smart devices. mPOS enables smaller business owners to accept card payments without having to invest in electronic cash registers or pay for software support. mPOS devices are considerably less expensive than their traditional counterparts and rely on cloud-based subscription models, making them even more cost-effective. Establishments with conventional countertop POS systems are known to deploy mPOS during rush or heavy traffic times to streamline customer service and avert backups at cash registers. mPOS technology also has the potential to amplify sales by helping companies finalise deals anywhere in their store or exhibition area, hence capitalising on immediate interest and excitement. Investing in mPOS limits a business’s liability as all financial operations are encrypted, and debit and credit information isn’t stored on the devices. Not only does this reduce the potential of security breaches, but this data storage technique ensures compliance with different privacy and security regulations, like PCI DSS. mPOS also enables smaller companies to benefit from security technologies and monitoring through their software vendors, a perk that was once exclusive to large organisations.mPOS Evolution
Since the introduction of mPOS, the demand for the technology has constantly been growing. In 2018, an estimated 28 billion transactions were made through mPOS devices. Experts expect the number of operations to increase threefold by the end of 2023, reaching over 87 billion transactions. Furthermore, they predict that mPOS operations will represent approximately 24% of all POS transactions worldwide. Research shows that an mPOS device’s average price will likely drop by the end of 2023. This will make the technology even more attractive to smaller or cash-driven businesses that have lost customers due to offering singular payment options. The implementation of biometrics (fingerprints and face recognition) to confirm identities during mPOS payments will further cement the technology’s reputation as a dependable method for executing financial transactions. In 2023, only 4% of the deployed mPOS devices use biometrics, but the number is expected to rise in upcoming years.SOFTPOS Technology
Software Point-of-Sale (SOFTPOS) is a revolutionary technology that transforms smart devices into contactless payment terminals. It allows businesses to directly accept transactions on their smartphones or tablets without the need for any additional hardware, as long as the devices are Near Field Communication (NFC) enabled. SOFTPOS is typically bank and device agnostic, meaning it can work with any bank, acquirer, or NFC-enabled phone or tablet. It helps merchants to accept financial operations from contactless payment cards or e-wallets, like ApplePay, SamsungPay, or Android Pay. Certain SOFTPOS solutions are developed to accept multiple payment methods through various communication channels supported by smart devices. For example, companies can use phone cameras to accept QR-based payments from digital wallets, such as Alipay, WeChat, phyre, etc. Transactions are processed, authorised, and reconciled over cellular networks. The technology aims to level the playing field for businesses by giving them the possibility to improve customer loyalty and accept digital payments without making massive investments in acquiring and maintaining conventional POS systems. SOFTPOS offers the same advantages as mPOS technology, with the main difference being that companies won’t need to get or purchase hardware such as card readers and barcode scanners to execute sales.How Does SOFTPOS Work
SOFTPOS technology enables users to download an application, register, select an acquiring bank, and start accepting transactions on their personal devices. Consumers make payments by holding their wearables, e-wallets, or contactless cards near (up to 4cm) the smartphone or tablet. The technology suits all types of businesses, from market stalls, contractors, and food trucks to large brick-and-mortar establishments that wish to offer checkout services on the shop floor to help their clients avoid queuing.The Concept Behind SOFTPOS
Undoubtedly, SOFTPOS solutions provide companies and customers with many benefits. The concept holds promise for approximately 180 million micro and small businesses worldwide, where fewer than 10% in numerous emerging markets can currently accept digital payments. The idea is to develop the technology beyond conventional in-store payments. Developers strive to make SOFTPOS a reliable solution that could include transit and eCommerce, where the functionality could be part of the application, allowing consumers to tap their contactless cards on their own devices to make or authenticate payments instead of entering their card details.SOFTPOS Compliance
As with all payment technology, SOFTPOS manufacturers must ensure their product meets relevant compliance protocols and can provide safe and secure transactions. This means achieving Level 1 certification in line with the EMV® Contactless Communication Protocol Specification for contactless payments. Level 1 tests ensure contactless devices meet analogue and digital requirements, such as lower-level electromagnetic field and communication protocols, including operational distance tests. Even though Level 1 certification is crucial, SOFTPOST developers must overcome different challenges compared to traditional POS manufacturers to evaluate whether their products align with the latest regulations. Conventional POS systems are certified in tune with EMV® Proximity Coupling Device (PCD) Level 1 requirements. This process cannot be applied to SOFTPOS solutions because of the differences between smart devices and payment terminals. In truth, compliance procedures have not caught up yet with the technology, but this is expected to change in the foreseeable future. SOFTPOS manufacturers can currently request approval through the EMVCo’s Early Adopter Programme. It evaluates mobile devices with the built-in capability for contactless payment acceptance. By completing the program, developers can ensure that their technology meets relevant MVCo Level 1 requirements. However, it’s important to note that the process isn’t obligatory for SOFTPOS solutions, meaning companies should be cautious about the devices they choose to deploy the technology on.SOFTPOS Security
Two essential security elements that SOFTPOS developers must ensure are in place are monitoring and attestation. They are used to check the security and integrity of the technology thoroughly. The procedure is simple – the application constantly sends data about its status to the attestation and monitoring back-end, which verifies the information and confirms that the app’s integrity hasn’t been corrupted. Other software-based security solutions that can be applied to SOFTPOS are:- Anti-Rooting
- Anti-Instrumentation
- White-Box Cryptography
- Anti-Tampering
- Device-Binding
- Obfuscation
- Anti-Debugging
- Anti-Emulation
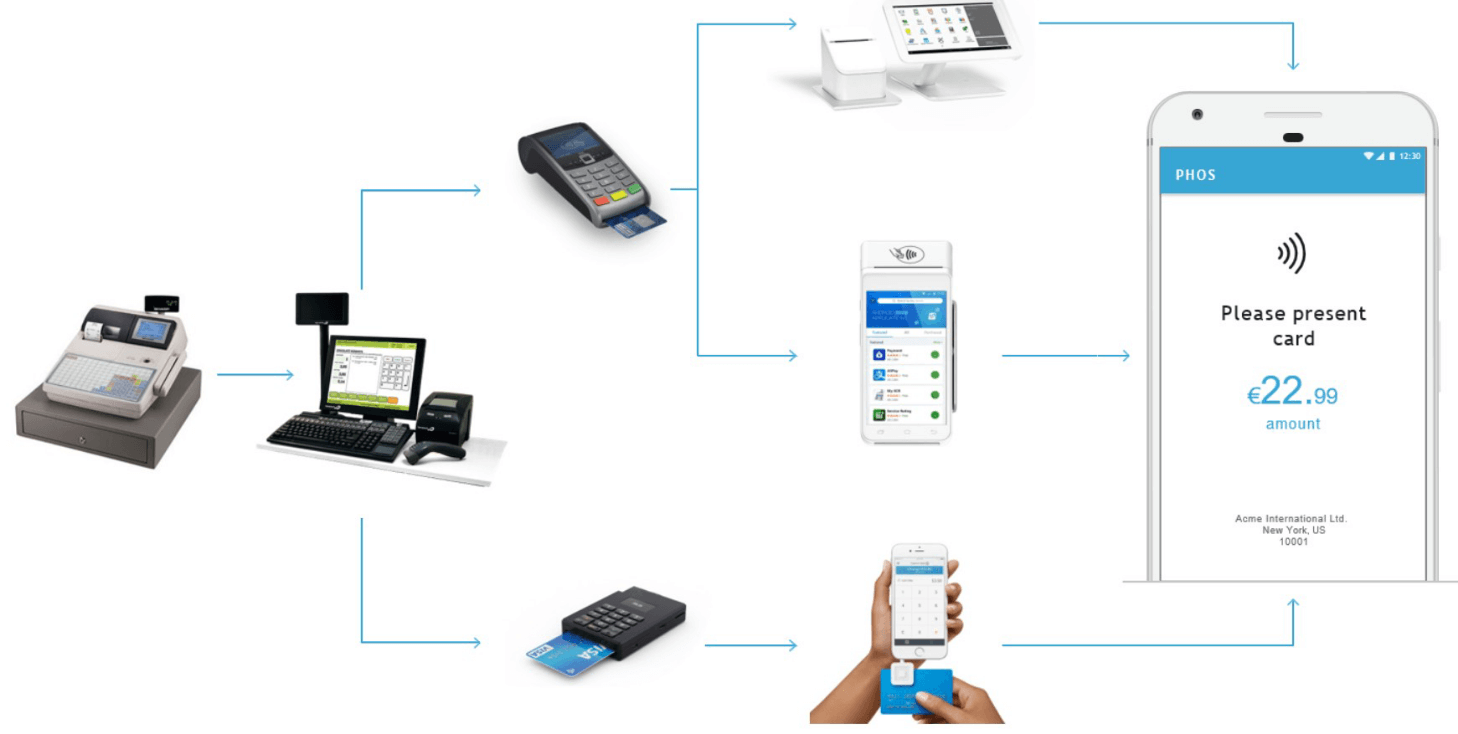
Evolution of POS Technology